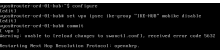
There is a previous ticket, but looks like there was an issue replicating:
https://phabricator.vyos.net/T2606
I have some additional information that could help narrow down the source of this error.
VyOS version: VyOS 1.3-beta-202112080938
Here is when I receive this error:
- I am setting up DMVPN, using GRE tunnels, with the mode as Transport where mobike = disable, causes the SWANCTL not to load the config
- On another machine I have a regular site to site VPN (not using GRE tunnels), with the mode as tunnel, where mobike = disable causes no issue
I will attach my config that triggers the issue and can try to help narrow down the issue
Not working with MOBIKE = disabled
//configuration is for the hub - DMVPN
#set ipsec interface
set vpn ipsec ipsec-interfaces interface 'eth0'
#configure ipsec
set vpn ipsec esp-group "ESP-HUB" compression 'disable'
set vpn ipsec esp-group "ESP-HUB" lifetime '3600'
set vpn ipsec esp-group "ESP-HUB" mode 'tunnel'
set vpn ipsec esp-group "ESP-HUB" pfs 'dh-group21'
set vpn ipsec esp-group "ESP-HUB" proposal 1 encryption 'aes256'
set vpn ipsec esp-group "ESP-HUB" proposal 1 hash 'sha256'
set vpn ipsec esp-group "ESP-HUB" proposal 2 encryption 'aes256'
set vpn ipsec esp-group "ESP-HUB" proposal 2 hash 'sha256'
set vpn ipsec ike-group "IKE-HUB" ikev2-reauth 'no'
set vpn ipsec ike-group "IKE-HUB" key-exchange 'ikev2'
set vpn ipsec ike-group "IKE-HUB" lifetime '28800'
#set vpn ipsec ike-group "IKE-HUB" mobike 'disable'
set vpn ipsec ike-group "IKE-HUB" proposal 1 dh-group 21
set vpn ipsec ike-group "IKE-HUB" proposal 1 encryption 'aes256'
set vpn ipsec ike-group "IKE-HUB" proposal 1 hash 'sha256'
set vpn ipsec ike-group "IKE-HUB" proposal 2 dh-group 21
set vpn ipsec ike-group "IKE-HUB" proposal 2 encryption 'aes256'
set vpn ipsec ike-group "IKE-HUB" proposal 2 hash 'sha256'
set vpn ipsec logging log-level 1
set vpn ipsec logging log-modes dmn
set vpn ipsec logging log-modes mgr
set vpn ipsec logging log-modes knl
set vpn ipsec logging log-modes net
###################GRE tunnel configuration#################
#change for each hub
#the tunnel 172.x.x.x address - IP for the tun0 interface
set interfaces tunnel tun0 address "${TUNNEL_IP_WITH_MASK}"
set interfaces tunnel tun0 encapsulation 'gre'
set interfaces tunnel tun0 multicast 'enable'
set interfaces tunnel tun0 parameters ip key '1'
#floating WAN IP - this must be fixed for the HUB - eth ETH0 IP
set interfaces tunnel tun0 source-address "${WAN_FLOATING_IP}"
#IPSEC profile
set vpn ipsec profile NHRPVPN authentication mode 'pre-shared-secret'
#using orange for testing
set vpn ipsec profile NHRPVPN authentication pre-shared-secret "${PRE_SHARED_KEY}"
set vpn ipsec profile NHRPVPN bind tunnel 'tun0'
set vpn ipsec profile NHRPVPN esp-group 'ESP-HUB'
set vpn ipsec profile NHRPVPN ike-group 'IKE-HUB'
#NHRP
set protocols nhrp tunnel tun0 cisco-authentication 'orange'
set protocols nhrp tunnel tun0 holding-time '300'
set protocols nhrp tunnel tun0 multicast 'dynamic'
set protocols nhrp tunnel tun0 redirect
set protocols nhrp tunnel tun0 shortcutWorking with MOBIKE - just a site-to-site VPN
set vpn ipsec esp-group ESP-${SUFFIX} compression disable
set vpn ipsec esp-group ESP-${SUFFIX} lifetime 3600
set vpn ipsec esp-group ESP-${SUFFIX} mode tunnel
set vpn ipsec esp-group ESP-${SUFFIX} pfs disable
set vpn ipsec esp-group ESP-${SUFFIX} proposal 1 encryption aes256
set vpn ipsec esp-group ESP-${SUFFIX} proposal 1 hash sha1
set vpn ipsec esp-group ESP-${SUFFIX} proposal 2 encryption aes256
set vpn ipsec esp-group ESP-${SUFFIX} proposal 2 hash sha1
set vpn ipsec ike-group IKE-${SUFFIX} close-action restart
set vpn ipsec ike-group IKE-${SUFFIX} ikev2-reauth no
set vpn ipsec ike-group IKE-${SUFFIX} key-exchange ikev2
set vpn ipsec ike-group IKE-${SUFFIX} lifetime 28800
set vpn ipsec ike-group IKE-${SUFFIX} mobike disable
set vpn ipsec ike-group IKE-${SUFFIX} proposal 1 dh-group 21
set vpn ipsec ike-group IKE-${SUFFIX} proposal 1 encryption aes256
set vpn ipsec ike-group IKE-${SUFFIX} proposal 1 hash sha1
set vpn ipsec ike-group IKE-${SUFFIX} proposal 2 dh-group 21
set vpn ipsec ike-group IKE-${SUFFIX} proposal 2 encryption aes256
set vpn ipsec ike-group IKE-${SUFFIX} proposal 2 hash sha1
#use eth0 that has the floating IP address
set vpn ipsec ipsec-interfaces interface eth0
set vpn ipsec logging log-level 1
set vpn ipsec logging log-mode dmn
set vpn ipsec logging log-mode mgr
set vpn ipsec logging log-mode knl
set vpn ipsec logging log-mode net
set vpn ipsec site-to-site peer ${PEER_IP} authentication id ${FLOATING_IP}
set vpn ipsec site-to-site peer ${PEER_IP} authentication mode pre-shared-secret
set vpn ipsec site-to-site peer ${PEER_IP} authentication pre-shared-secret ${PSK_SECRET}
set vpn ipsec site-to-site peer ${PEER_IP} authentication remote-id ${PEER_IP}
set vpn ipsec site-to-site peer ${PEER_IP} connection-type respond
set vpn ipsec site-to-site peer ${PEER_IP} default-esp-group ESP-${SUFFIX}
set vpn ipsec site-to-site peer ${PEER_IP} description "my description"
set vpn ipsec site-to-site peer ${PEER_IP} ike-group IKE-${SUFFIX}
set vpn ipsec site-to-site peer ${PEER_IP} ikev2-reauth inherit
set vpn ipsec site-to-site peer ${PEER_IP} local-address ${FLOATING_IP}
set vpn ipsec site-to-site peer ${PEER_IP} tunnel 0 allow-nat-networks disable
set vpn ipsec site-to-site peer ${PEER_IP} tunnel 0 allow-public-networks disable
set vpn ipsec site-to-site peer ${PEER_IP} tunnel 0 local prefix ${VPC_NETWORK}
set vpn ipsec site-to-site peer ${PEER_IP} tunnel 0 remote prefix ${REMOTE_SUBNET_WITH_CIDR}