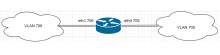
When a bridge connects subinterfaces of different VLANs (eth0.705 & eth1.706 for example), STP messages from one VLAN go to the other VLAN. This causes port blocking on the switches.
The solution which is used in Cisco ASA is the modification of the host numbers in the STP messages (pcap files attached, see the latest STP packets).
nftables allows to do this in VyOS (thanks to @zsdc for the example of nft rules):
sudo nft add table bridge br1
sudo nft add chain bridge br1 vlan_change_705 { type filter hook postrouting priority 300 \; policy accept \; }
sudo nft add rule bridge br1 vlan_change_705 meta oifname eth0.705 ether daddr 01:00:0c:cc:cc:cd @nh,384,16 706 @nh,384,16 set 705
sudo nft add table bridge br1
sudo nft add chain bridge br1 vlan_change_706 { type filter hook postrouting priority 300 \; policy accept \; }
sudo nft add rule bridge br1 vlan_change_706 meta oifname eth1.706 ether daddr 01:00:0c:cc:cc:cd @nh,384,16 705 @nh,384,16 set 706It would be useful to add this feature to the VyOS bridge or firewall settings