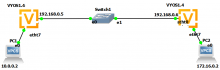
I noticed that the two peer tunnel will broken when esp timeout (I used 30 sec to check it faster).
Even if I set DPD and close-action as restart, it would not reconnect ever.
IPsec will show the connection is ESTABLISHED but it will not go to INSTALLED step.
This is very easy to reproduce, just connecting two vyos by ipsec then set the esp timeout very low, and it will be.
Is it a bug or my config is wrong ? please help me.
The ike and esp config like these:
esp-group default {
lifetime 30
mode transport
pfs dh-group2
proposal 1 {
encryption aes128
hash sha1
}
}
ike-group default {
close-action restart
dead-peer-detection {
action restart
}
key-exchange ikev1
lifetime 86400
proposal 1 {
dh-group 14
encryption aes128
hash sha1
}
}
site-to-site {
peer <right> {
authentication {
mode pre-shared-secret
pre-shared-secret myipseckey
}
default-esp-group default
ike-group default
local-address <left>
tunnel 0 {
esp-group default
}
}
}